AWS run tasks on EC2 without SSH, AWS Systems Manager
There are many ways to deploy your application or run commands inside EC2 instance. But to avoid security related threats ssh must be blocked(imho). Even inside private vpc its always good to be careful. AWS has a tool for this purpose and its called Systems Manager. It can do a lot of things besides accessing EC2 instance and do stuff inside. But this post will be about Systems Manager Documents.
First of all we need to give EC2 instances necessary IAM policy which is ssmfullaccess. After that we can create our instance using cli/console/sdk. But we dont open ssh port to anywhere on internet or vpc. In this post because i was used Amazon Linux 2 i dont need to download and install amazon ssm-agent. This tool is used for connecting and executing our commands to instance.
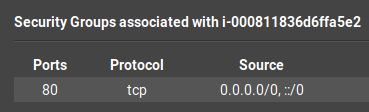
After this stage we should define our ssm-document. System Managers allows us to github,s3 or define on console actions for this. But i created a github repo and uploaded there.
Then we select our instance from tags or manually. There is last section and its for ssm logs. I choosed s3 bucket for logs. It’s so useful for debugging. Also you can use sns notification for success or failing commands to get notified.
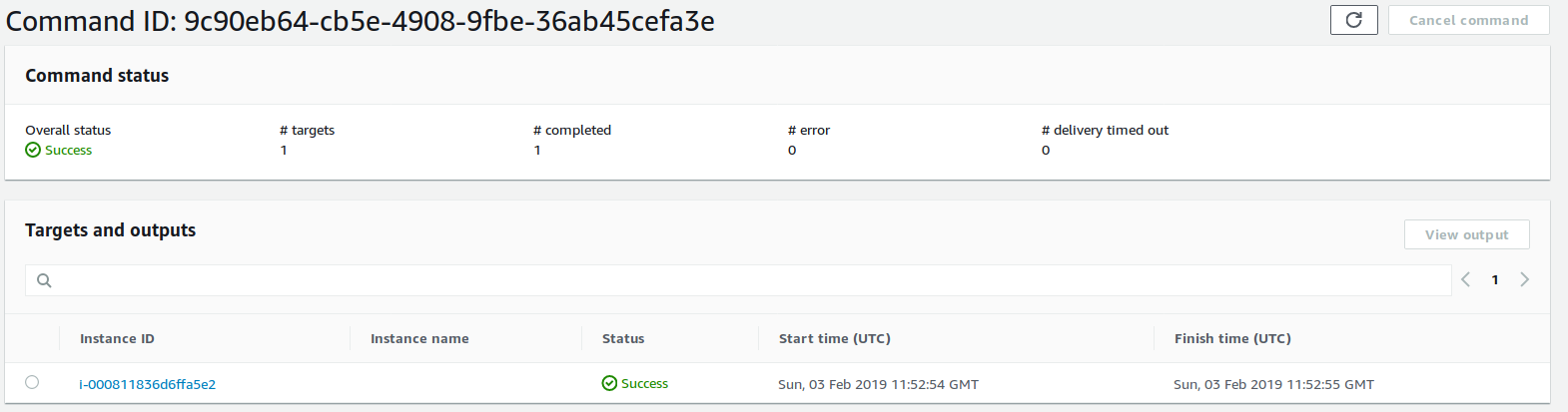
And command works successfully. Created nginx without accessing instance manually or using ssh.